Enabling Secure Innovation in Medical Devices
ELTON AI
One Fee. One Platform. Total Compliance.
Request a Platform Walkthrough

Overview
MedTech Cybersecurity Copilot
ELTON is a pre-validated medical device vulnerability platform built on more than a decade of hands-on experience with the FDA. The platform delivers every FDA-required testing activity with validated output. Using a digital twin, attack path analysis, vulnerability chaining, and remediation optimization, ELTON delivers precise, context-aware results that reflect real-world exploitability. ELTON transforms complex vulnerabilities into clear, actionable insight, helping teams focus on the vulnerabilities that truly matter.
Remediate less through a solution that maintains full traceability and defensibility as an FDA-Approved Medical Device Design Tool
Request a Platform Walkthrough
Contact Us
ELTON AI Identifies Vulnerabilities That Matter
Support vulnerability decisions with a traceable, FDA-approved solution.
AI-Enabled Product Security, Delivered as a Service.
ELTON ONE
One Platform. Total Compliance.
ELTON ONE is a subscription partnership that fulfills all FDA vulnerability compliance requirements for modern devices, providing on-demand visibility, posture management, and regulatory reporting across every product release.
Platform Capabilities
ELTON platform is an integrated vulnerability discovery service to deliver traceable, defensible results across a variety of vulnerability sources.
Discover
Context Matters. ELTON first creates a digital twin to transform target architecture and security control data into a graph for actionable intelligence.
Identify
ELTON executes testing. Effective triage links pen testing, SAST/DAST, SBOM CVEs, real-time risk, and machine-readable vulnerability data.
Contextualize
ELTON adjusted ratings by mapping findings to architecture, adjusting for context, correlating sources, and evaluating chained exploitability across components.
Monitor
ELTON continuously monitors materials, integrates test results, and adjusts vulnerability ratings in response to new vulnerabilities or posture context.
Optimize
Perform ‘what if’ analyses to identify packages of vulnerabilities to remediate, and if fixed, their impact on overall posture for better decision-making.
Compliance Requirements
ELTON streamlines vulnerability compliance by automating triage that typically requires a small team of experts.
FDA Premarket Requirements
ELTON fulfills premarket vulnerability testing requirements, ensuring accurate, defensible vulnerability ratings aligned with documentation and regulatory expectations.
Secure Product Development Framework
ELTON operationalizes a SPDF by integrating vulnerability data with security design, threat modeling, and vulnerability management during development.
FDA Postmarket Requirements
ELTON meets FDA postmarket guidance by automating continuous vulnerability identification, triage, threshold alerts, and metric collection across product lifecycles.
Total Product Lifecycle Management
ELTON delivers a unified view to manage vulnerability compliance across every product, model, and release—ensuring coverage through end-of-life.
Patch Optimization & No-Fix Defensibility
Identify high-impact fixes and generate evidence showing vulnerabilities are unexploitable or unreachable enabling compliance without unnecessary patching.
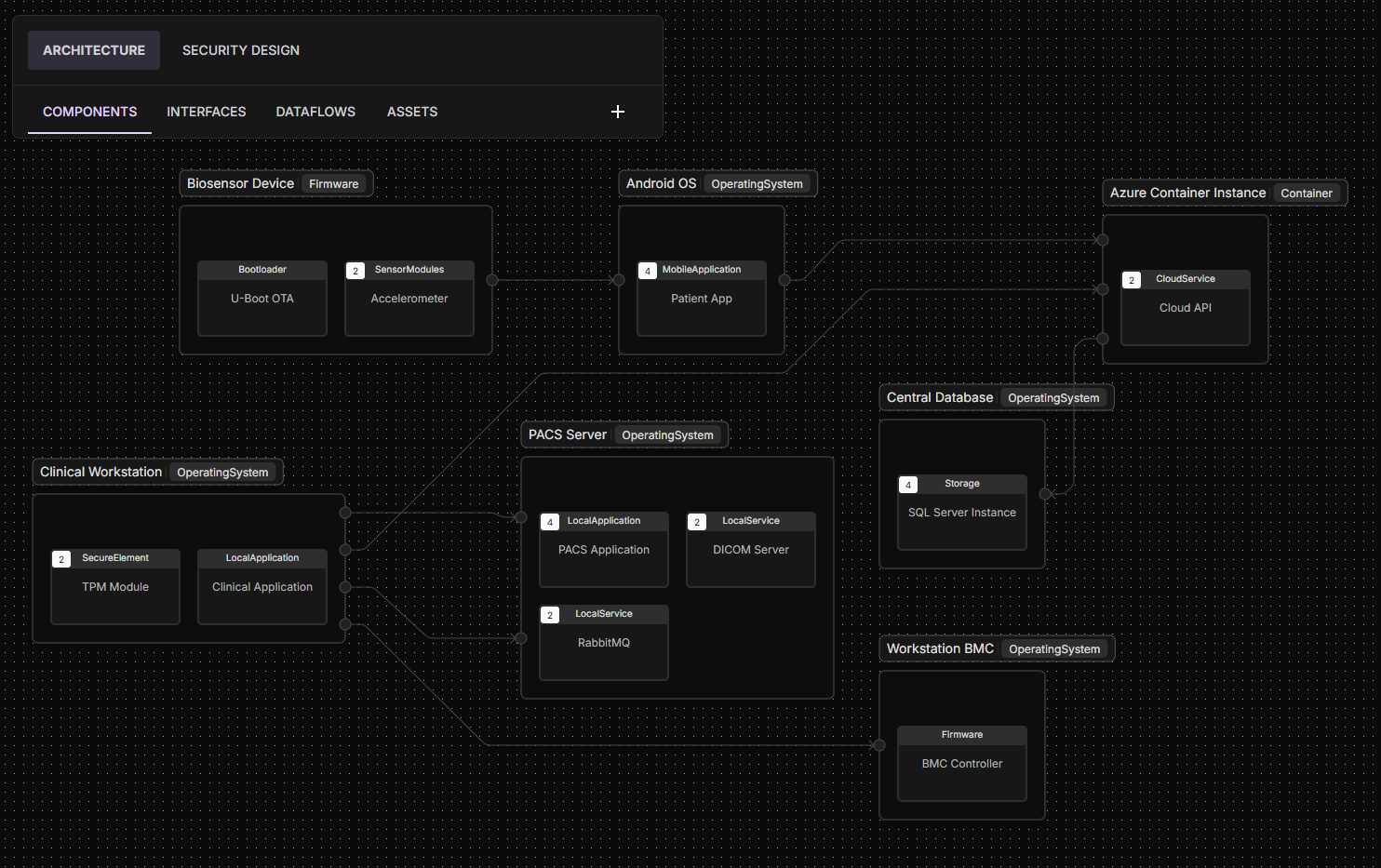
Product-Aware Analysis
Automated Vulnerability Scoring for Your Unique Medical Device
ELTON performs architecture-aware vulnerability analysis tailored to your specific product design. It maps complete attack paths between exposed attack surfaces and downstream vulnerabilities, traversing software components, AI pipelines, dataflows, and system trust boundaries. By simulating real-world adversarial movement, ELTON determines whether a vulnerability is simply present or truly exploitable within your device context.
Request a Platform Walkthrough
NextGen Devices Must
Meet AI-Enabled Device Regulations
FDA’s January 2025 AI-Enabled Device draft guidance identifies 7 AI-specific cyber threats that manufacturers must address in premarket submissions, including data poisoning, model inversion, evasion, data leakage, overfitting, bias manipulation, and performance drift. Only one of those seven, model evasion, is primarily a runtime concern. The guidance makes clear that testing the deployed model alone isn’t sufficient, manufacturers need to demonstrate threat and testing coverage across the full AI system lifecycle.
This isn’t just “test the model.” This is “test everything that touches the model.”
Request a Platform Walkthrough
Future is
Product-as-Code
Product-as-code is the future standard for traceably expressing product architecture and cybersecurity posture to regulators and customers. It enables accurate vulnerability analysis and risk evaluation especially critical in the AI era. ELTON creates product-as-coded out of every product, model, and release to ensure a proper cybersecurity view and on-going posture management. Vulnerability findings can be overlayed on a Product-as-Code for an extensible reporting output.
Request a Platform Walkthrough
Intelligence
Where Industry Expertise Meets AI Automation
ELTON is powered by insights from over a decade of medical device testing expertise and 1000+ FDA-approved submissions. View FDA Cybersecurity Guidance

No Additional Tools. One Intelligent Solution.
ELTON reduces cost by including all vulnerability needs, eliminating unnecessary patching, and automating the most resource-intensive vulnerability management tasks. Achieve full compliance without expanding headcount.
Request a Platform Walkthrough
