Platform Capabilities
Medical Device Cybersecurity Surveillance
Continuous vulnerability surveillance in alignment with FDA requirements, focusing on issues that present the most regulatory risk with an FDA-Approved Methodology.
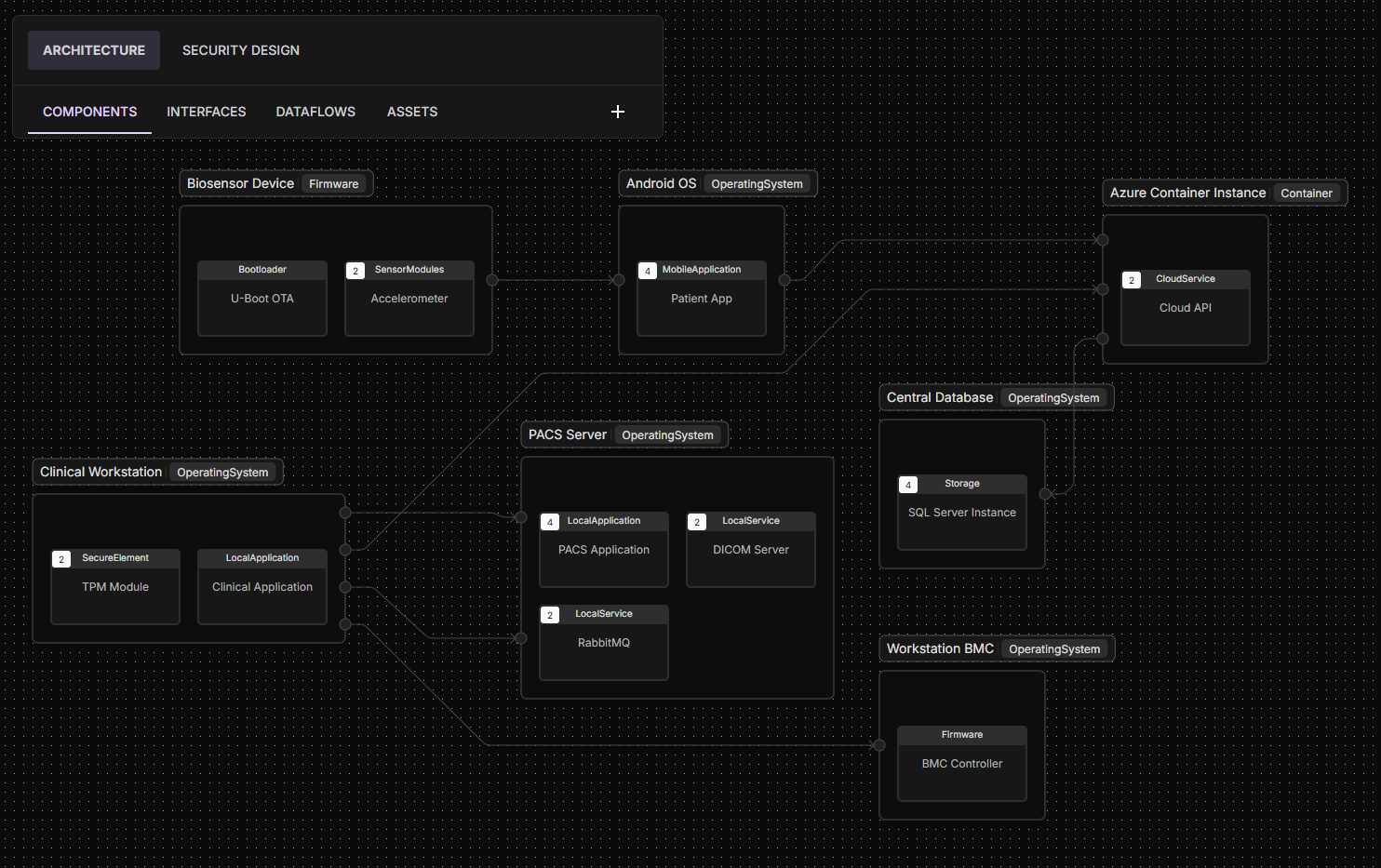
Overview
X-Ray your Software and Avoid Patching
ELTON x-rays your product by determining the software ingredients and combining them with runtime insights.
It enriches intelligence by mapping each ingredient to its exact location within your product’s architecture, down to the specific software module or hardware interface it touches.
This attacker-oriented, relationship-based view focuses not only on whether a vulnerable function exists, but whether it’s exploitable in your product. If the component sits in an isolated or protected area, ELTON deprioritizes the risk, giving you clarity on what truly matters.
Digital Twin
Product-Adjusted Exploitability
Most vulnerabilities aren’t exploitable in your specific product or release. ELTON automates exploitability analysis to get the rating right, and automates verification of high or critical vulnerabilities before acting.
Defensible Decissions
ELTON replaces costly, error-prone analysis, determining if a software component is truly exploitable and to what severity, reducing noise from low-impact vulnerabilities and defensibly pushing back on CVEs to regulators.
Contact Us
1% of Vulnerabilities Actually Matter
Focus on the Vulnerabilities That Impact Regulatory Risk
Make Sure They’re Rated Accurately
Your Product Contains Hundreds of Vulnerabilities
ELTON fulfills FDA premarket and postmarket cybersecurity expectations by enriching SBOMs alongside other vulnerability sources, continuously monitoring for new CVEs, and determining if mitigation is required. It supports CAPA by documenting why unpatched SBOM issues are justified, ensuring manufacturers meet regulatory demands with defensible, risk-based analysis across all software components and product architectures. No SMEs required, fully automated.
Regulatory-Aligned SBOM
ELTON generates a product-specific SBOM enriched with architectural and runtime data to fulfill 2025 FDA Premarket Cybersecurity Guidance expectations for Vulnerability Management SOPs. Each ingredient is linked to a component, interface, and trust boundary providing a defensible baseline to track, investigate, and justify vulnerabilities throughout the product lifecycle.
Prioritized Monitoring
ELTON continuously monitors your SBOM against CVE databases and maps those findings to your product’s digital twin, fulfilling the 2016 FDA Postmarket Cybersecurity Guidance to assess whether a vulnerability truly requires remediation. ELTON highlights which issues are not exploitable based on architecture and defensibly deprioritizes.
CAPA and Audit Readiness
With ELTON, unresolved SBOM findings are not an ignored audit timebox, they’re contextualized, rated, and documented using the FDA-approved Rubric for Applying CVSS to Medical Devices. This fulfills CAPA obligations by ensuring every issue has a traceable justification, even if left unpatched.
Avoid Vulnerability Debt
Preempt the thousands of CVEs each product release can generate before they accumulate into unmanageable technical debt. ELTON filters noise, prioritizes real risk, and prevents costly, unnecessary remediation work.
Advisories
We Track Down Zero-Day CVEs
Our cybersecurity researchers have identified and disclosed multiple zero-day Common Vulnerabilities and Exposures (CVEs) in networks, devices, and related software.
Verizon MiFi Invalidated CSRF Token for File Uploads
Impact: High
HtmlImport Unauthenticated Remote Code Execution
Impact: High
Compliance Insights
Power Your Postmarket Maintenance with Intelligence
ELTON Copilot is built on insights and data from the field. View more insights

Lowest Cost of Cybersecurity Maintenance.
ELTON delivers better vulnerability monitoring through context and defensibility with an FDA-Approved approach.
